Network Visibility & Monitoring
Managing Your Network — It's Complicated
Your network is a complex tangle of routers, switches, and ports — both physical and virtual. It’s on premises, in private and public clouds, and at remote sites. It’s also a host of tools — APM and NPM, SIEMs, firewalls — all hungry for network data. You’ve got to manage it all, as well as pass vital data to security analysts and comply with changing regulations. It’s complex, but MBUZZ is here to help. Our comprehensive set of network visibility, analytics and optimization solutions goes beyond aggregating traffic and passing it to tools. It also includes:
- Broad and deep visibility across your private, public and hybrid cloud environments
- Layer 7 visibility to identify applications and reveal app and user behavior
- Rich application and protocol metadata to enable deeper analytics and more effective monitoring and security tools
Learn more about Network Visibility & Monitoring from MBUZZ
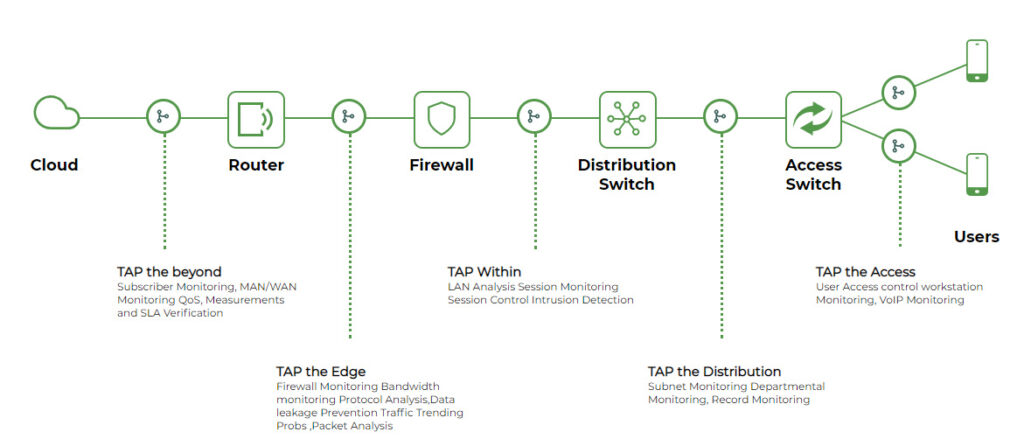
SEE HOW WE DRIVE NETWORK VISIBILITY AND ANALYTICS ON ALL TRAFFIC
Putting NetOps Back in Control
Degraded performance, oversubscribed tools, and ever-increasing costs. Sound familiar? Change this narrative:
Balance traffic over multiple monitoring and security tools
When several security tools are deployed, load balancing can optimize the response time and avoid uneven load while another is idling. By distributing the traffic load evenly among the available security tools, they are used in the most efficient way. A Network Packet Broker is an ideal tool for this as it sits between the TAPs and security tools.
The Key for Keeping Your Network Safe and Secure
Bypass TAPs provide fail-safe access for active in-line network security and performance tools. If an active in-line tool becomes unavailable, either due to a hardware malfunction, power loss, software problem, or planned maintenance, bypass TAPs ensure the network link stays operational.
Packet-level visibility into your virtual traffic
vTAP provides complete visibility of VM traffic (including inter-VM) for security, availability, and performance monitoring. Within the span of a decade, the use of server virtualization has become a standard industry practice. To gain visibility in virtual traffic and forward filtered network traffic to network security and network monitoring tools, you need a Virtual TAP (vTAP).
ACROSS PHYSICAL AND VIRTUAL INFRASTRUCTURES

Traffic Access
Access network traffic at key capture points in physical and virtual networks with the latest network TAPs

Managing & Optimizing Data Flow
Optimize data flow and maintain network flexibility with Network Packet Brokers

Traffic Capture & Analysis
Accelerate incident response and troubleshooting performance on premise or remotely














